ESET discovers watering hole attacks in the Middle East – Getting your life back on track after...
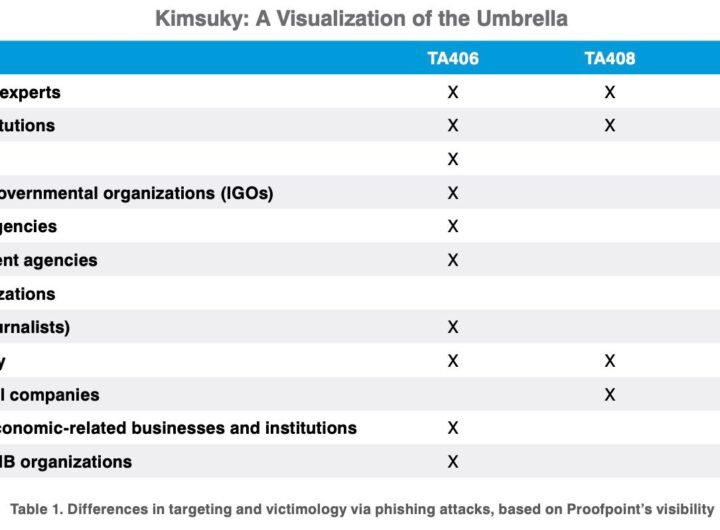
The TA406 group uses credential harvesting to target diplomats and policy experts in the United States, Russia,...
An indictment was unsealed charging two Iranian nationals for their involvement in a cyber-enabled campaign to intimidate...
Attackers also are deploying ProxyShell and abusing the vulnerabilities in stealthier manner, researchers say.
Lacework’s will use its $1.3 billion Series D to expand go-to-market strategies and its data-focused cloud security...
Security defenders can run these queries against Certificate Transparency logs to identify misconfigured SSL certificates before they...
Among other things, the pair pretended to be Proud Boys volunteers and sent in a fake video...
Zero trust isn’t a silver bullet, but if implemented well it can help create a much more...
The path out of the ransomware crisis is full inspection and protection of all traffic flows. That...
Security leaders can be treated as partners supporting the business and share accountability by establishing relationships with...