A previously unknown state-sponsored actor is deploying a novel toolset in attacks targeting telecommunication providers and IT...
The Cybersecurity and Infrastructure Security Agency (CISA), the Federal Bureau of Investigation (FBI), and the National Security Agency (NSA)...
The victims lost an average of nine days to downtime and two-and-a-half months to investigations, an analysis...
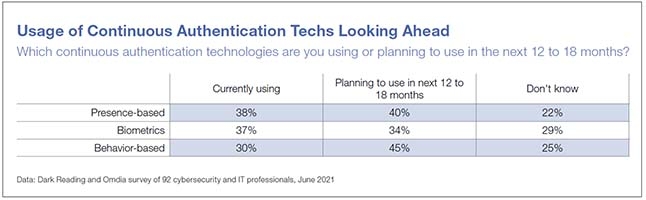
Security leaders are interested in continuous authentication technologies, especially behavioral-based capabilities.
A deep-dive study on the inner workings of incident response teams leads to a framework to apply...
Zero trust aims to replace implicit trust with explicit, continuously adaptive trust across users, devices, networks, applications,...
Remote Desktop aims to solve vulnerability issues with RDP by implementing robust access and security controls.
Deal will merge Bitglass’s security service edge technology with Forcepoint’s SASE architecture.
Graph databases can play a role in threat intelligence and unraveling sprawling data.
Startup created by former leaders of Microsoft Cloud Security Group experiencing rapid growth.