Prolific ransomware cybercrime group’s approach underscores a complicated, layered model of cybercrime.
With more staff working remotely, privileged access management (or PAM) has never been more important. Market forecasts,...
The last thing you want is a vendor that lies to you about its security practices.
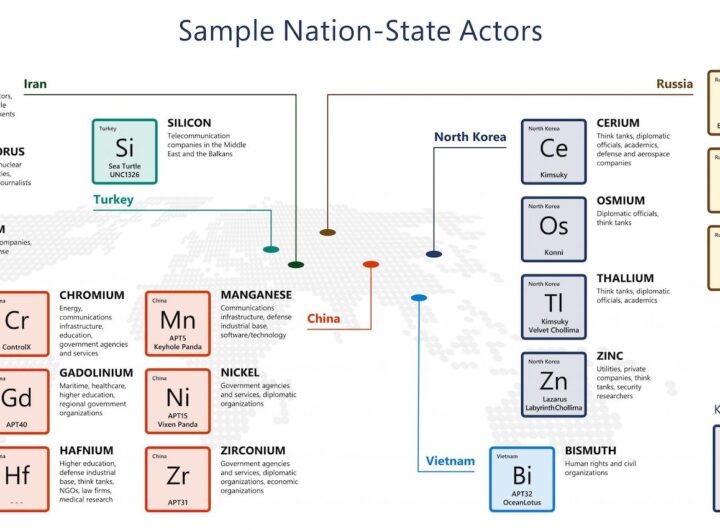
A wealth of Microsoft data highlights trends in nation-state activity, hybrid workforce security, disinformation, and supply chain,...
HP aims to let admins secure work-from-home endpoints by extending cloud security management that can remotely track,...
Continuous monitoring of network traffic, data loss prevention, and responsive self-healing protection from threats to cloud-native applications.
Une vulnérabilité a été découverte dans Stormshield Network Security. Elle permet à un attaquant de provoquer un...
De multiples vulnérabilités ont été découvertes dans les produits Cisco. Elles permettent à un attaquant de provoquer...
Unpatched Dahua cameras are prone to two authentication bypass vulnerabilities, and a proof of concept exploit that...
Microsoft has fixed a bug blocking some Azure Virtual Desktop (AVD) devices from downloading and installing monthly security via...