A vast majority of security professionals surveyed think any exploit will start with the endpoint.
How unauthorized users can exploit wireless infrastructures for covert communication.
Contrast’s platform detects and prevents against OWASP Top Ten risks from development to production with out-of-the-box policy...
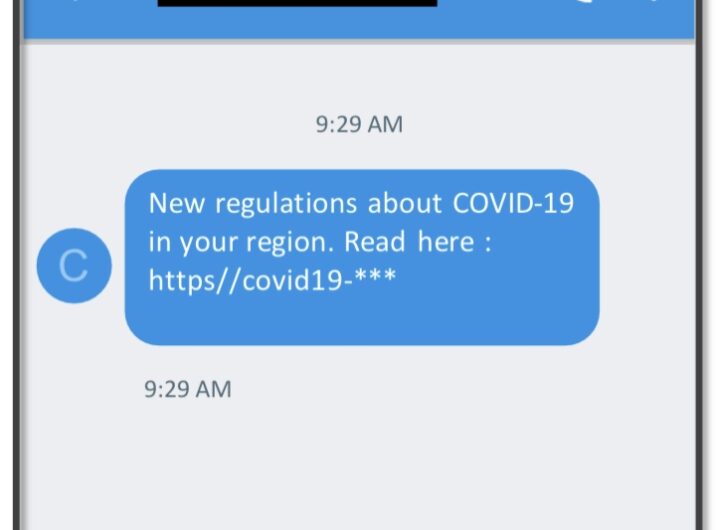
The attack targets Android devices and starts with a malicious SMS message that aims to bring malware...
While most US adults know they aren’t sufficiently protecting their data online, many find security time-consuming or...
Resilience shifts the focus toward eliminating the probable impact of the full attack chain.
The European Union has officially linked Russia to a hacking operation known as Ghostwriter that targets high-profile EU...
Microsoft is rushing to register Internet domains used to steal Windows credentials sent from faulty implementations of...
Google has released Chrome 94.0.4606.61 for Windows, Mac, and Linux, an emergency update addressing a high-severity zero-day vulnerability exploited in...
Exploit code that could be used for remote code execution on VMware vCenter Server vulnerable to CVE-2021-22005...