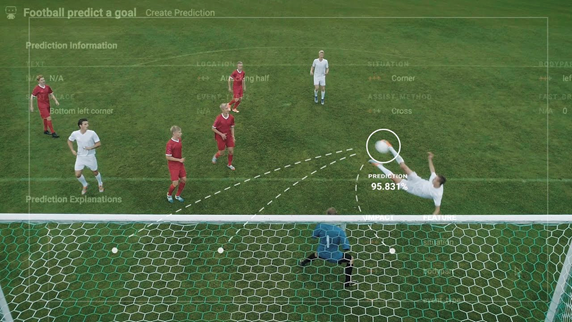
Attackers are harvesting credentials from compromised systems. Here’s how some commonly used tools can enable this.
Année : 2022
Security leaders from a media corporation, a commercial real estate company, and an automotive technology company share...
An anonymous Twitter user published yesterday a set of 10,000 API keys allegedly obtained from the 3Commas...
A bug in Google Home smart speaker allowed installing a backdoor account that could be used to...
How CISOs handle the ethical issues around data breaches can make or break their careers. Don’t wait...
An anonymous Twitter user published yesterday a set of 10,000 API keys allegedly obtained from the 3Commas...
Concerns about recessionary trends impacting the cybersecurity sector in 2022 remained largely unfounded in Q4, as investment...
Digital transformation initiatives are challenging because IT still has to make sure performance doesn’t suffer by making...
Malware operators have been increasingly abusing the Google Ads platform to spread malware to unsuspecting users searching for...
The Royal Ransomware gang claimed responsibility for a cyber attack against telecommunications company Intrado on Tuesday. […]