New functionality further reduces the risk of lateral movement.
Année : 2022
The quarterly report, made possible by its Dynamic Defense™ service, demonstrates significant progress in mitigating domain abuse...
Current authentication methods are based on the bearer model, but lack of visibility into the entities leveraging...
The simplicity and profitability of these attacks continue to appeal to threat actors a decade later.
A previously unnamed ransomware has rebranded under the name ‘Trigona,’ launching a new Tor negotiation site where...
The vulnerability, disclosed In October, gives an unauthenticated attacker a way to take control of an affected...
Organizations must be prepared to root out bad actors by any means possible, even if it means...
The new Microsoft Defender for Endpoint capabilities include built-in protection and scanning network traffic for malicious activity.
Internet Security Research Group (ISRG), the nonprofit behind Let’s Encrypt, says the open certificate authority (CA) has issued its...
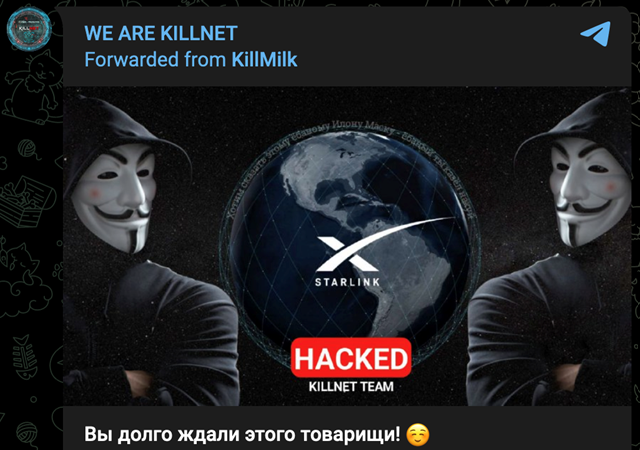
Elon Musk-owned Starlink, WhiteHouse.gov, and the Prince of Wales were targeted by Killnet in apparent retaliation for...