Organizations should balance process automation and human interaction to meet their unique security requirements.
Année : 2022
MoonBounce is the latest in a small but growing number of implants found hidden in a computer’s...
Accomplished cybersecurity leader will advocate globally for best practices in risk management and head up association security...
New Cybersecurity National Security Memorandum will let the spy agency « identify vulnerabilities, detect malicious threat activity and...
Implementing these and other security procedures will greatly improve the security posture of the United States and...
Threat actors from Eastern Europe seen expressing some concern about Russia being a safe place for them...
The acceleration of the digital transformation resulted in a surge of online transactions, greater adoption of digital...
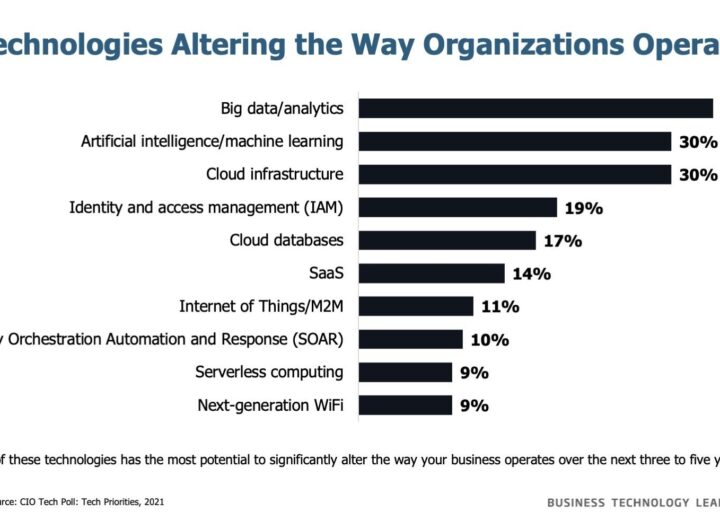
Security makes the top 10 list of technologies changing how organizations operate, an indicator of how information...
De multiples vulnérabilités ont été découvertes dans IBM Db2. Elles permettent à un attaquant de provoquer une...
De multiples vulnérabilités ont été découvertes dans les produits Cisco. Certaines d’entre elles permettent à un attaquant...