ThreatMapper 1.3.0 features secret scanning and the ability to enumerate a software bill of materials at runtime...
Mois : mars 2022
Paying a ransom might appear to be the best option, but it comes with its own costs.
Despite cost, it’s time to focus on securing legacy systems and physical infrastructure along with digital systems.
Agencies provide mitigation steps to protect satellite communication (SATCOM) networks amid « current geopolitical situation. »
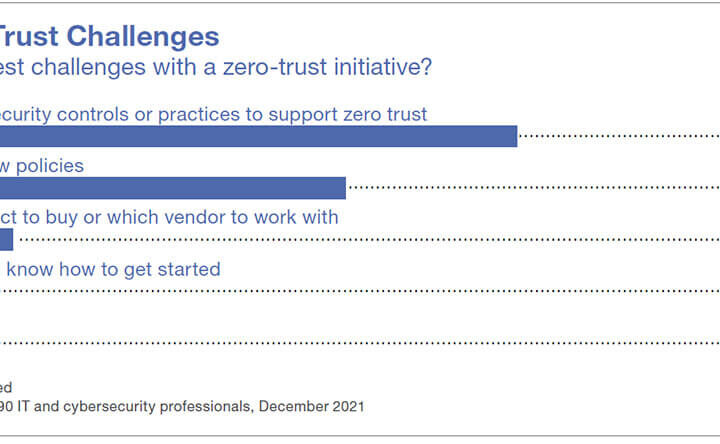
Nearly a third of respondents in a Dark Reading survey on endpoint security strategy say zero trust...
Report finds that 62 percent of IT decision makers have suffered a browser-based attack in the past...
CISA’s « Shields Up » alert provides urgency — and opportunity — for supply chain conversations.
Risk intelligence solution provides insight, visibility, and guidance to identify, prioritize, and remediate vulnerabilities like Log4j
The maintainer of a widely used npm module served up an unwelcome surprise for developers.
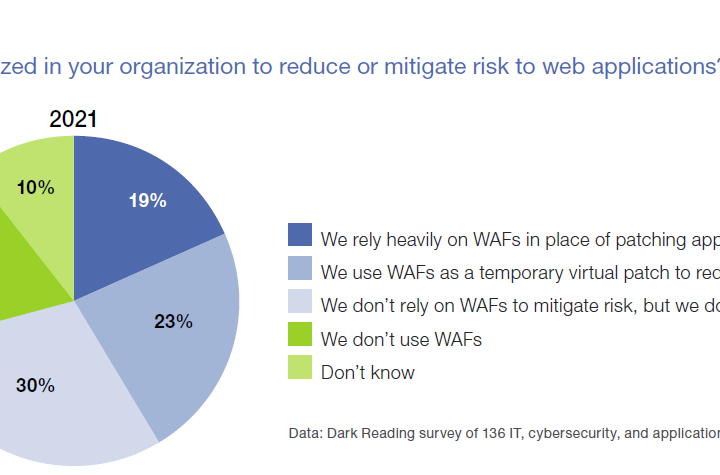
WAFs remain a popular backfill for complex and fraught patch management.