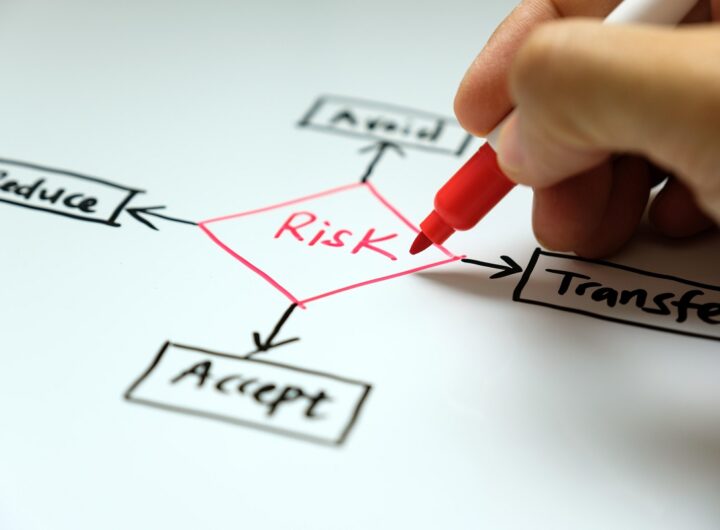
Risk-based vulnerability management solutions foster the convergence of risk management and vulnerability management. Andrew Braunberg explains what’s...
Mois : novembre 2022
The FBI warns that tech support scammers are now impersonating financial institutions’ refund payment portals to harvest...
Kaspersky is stopping the operation and sales of its VPN product, Kaspersky Secure Connection, in the Russian...
The stalling of federal legislation and the continued expansion of data brokers are fueling a phishing epidemic.
Cyberattackers like IPFS because it is resilient to content blocking and takedown efforts.
Hole-y software alert, Batman: Cybercriminal faves Citrix Gateway and VMware Workspace ONE have authentication-bypass bugs that could...
The malicious package downloads an image from the Web, then uses a steganography module to extract and...
Lacework Extends CNAPP Capabilities With Attack Path Analysis and Agentless Workload Scanning


1 min read
Greater insight into attack paths and runtime visibility helps customers reduce risk and improve cloud security posture.
Technology consolidates Windows and Linux software risk together in one UI, helping teams manage vulnerabilities and comply...
Links individual vulnerabilities to those known to have been used in ransomware operations, helping vulnerability management teams...