A bug in how Google Cloud Platform handles OAuth tokens opened the door to Trojan apps that...
Mois : avril 2023
The sensitivity of the personal information involved in the breach has yet to be determined by agency...
Mandiant found that North Korea’s UNC4736 gained initial access on 3CX’s network when an employee downloaded a...
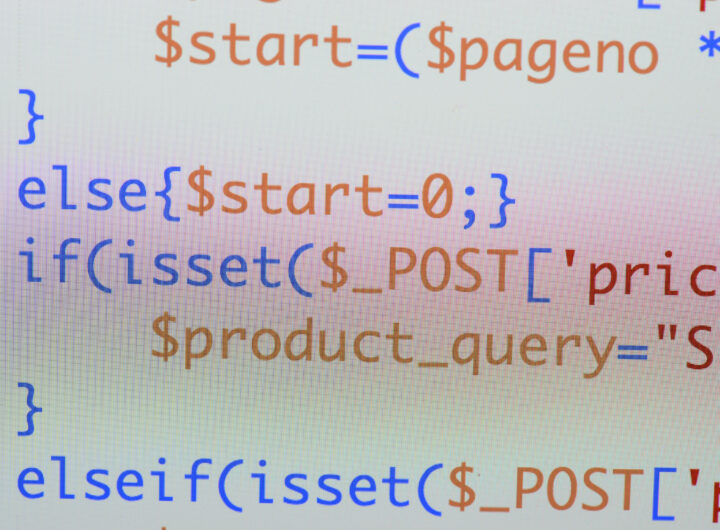
Attackers are using Eval PHP, an outdated legitimate WordPress plugin, to compromise websites by injecting stealthy backdoors. […]
Vulnerable MS-SQL database servers have external connections and weak account credentials, researchers warn.
Google’s Threat Analysis Group (TAG) has been monitoring and disrupting Russian state-backed cyberattacks targeting Ukraine’s critical infrastructure...
Overcoming the limitations of consumer MFA with a new flavor of passwordless.