Hackers break into the Bureau’s email systems to send out at least 100,000 emails warning recipients of...
ESET researchers have discovered strategic web compromise (aka watering hole) attacks against high‑profile websites in the Middle...
A victim of identity theft tells us how criminals used his identity to commit fraud and what...
US Government declassifies cybersecurity subjects they want you to learn about, and is hoping to pay you...
Not long ago, disinformation campaigns were rather unsophisticated. These days, however, threat actors put serious time and...
ESET discovers watering hole attacks in the Middle East – Getting your life back on track after...
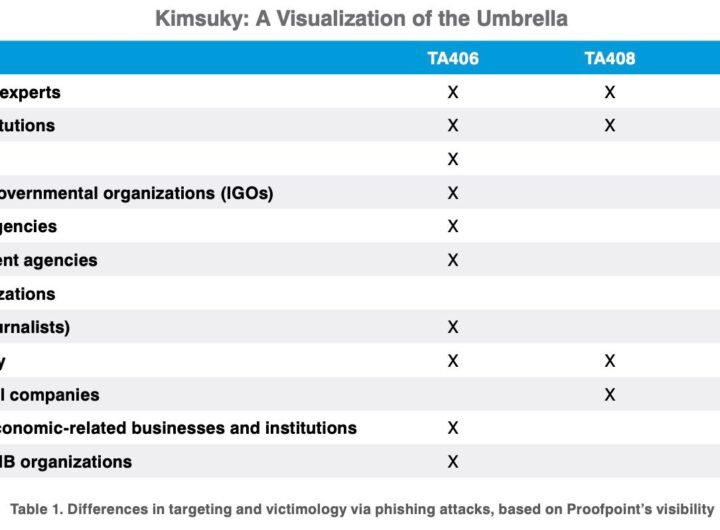
The TA406 group uses credential harvesting to target diplomats and policy experts in the United States, Russia,...
An indictment was unsealed charging two Iranian nationals for their involvement in a cyber-enabled campaign to intimidate...
Attackers also are deploying ProxyShell and abusing the vulnerabilities in stealthier manner, researchers say.
Lacework’s will use its $1.3 billion Series D to expand go-to-market strategies and its data-focused cloud security...