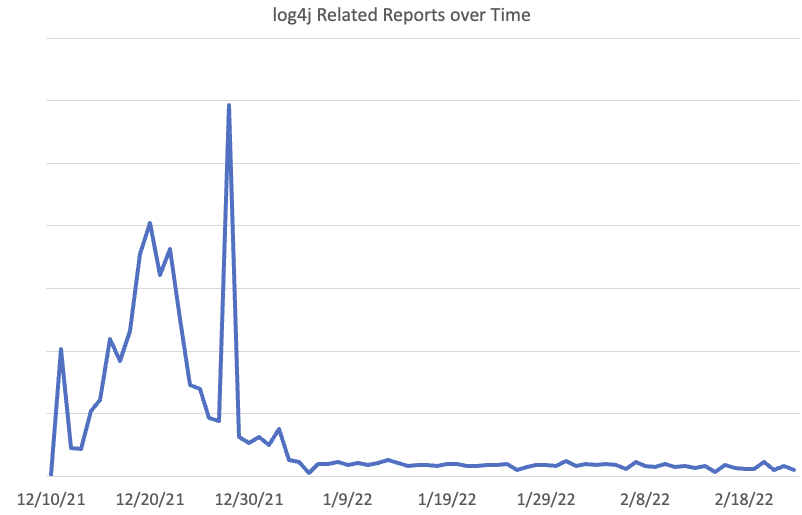
While attackers and researchers shift their attention to the next new vulnerability, security teams make sure they finish patching vulnerable Log4j versions in their applications and services.

While attackers and researchers shift their attention to the next new vulnerability, security teams make sure they finish patching vulnerable Log4j versions in their applications and services.
